Edge computing is distributed architecture methodology which brings some very specific advantages due to the distributed nature of the architecture. Using this architecture, businesses can enjoy benefits such as lower latency, reduced network bandwidth usage and near real-time processing of time-critical data.

But what is Edge Computing after all?
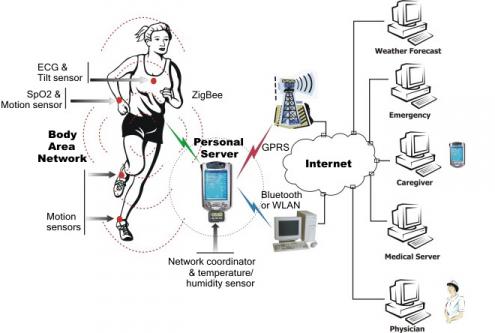
With the rise of IoT (Internet of things) we are having several sensors or devices located at multiple locations. These sensors collect a massive amount of data. The businesses need to analyze and use this data for further processing. If all sensors are to send data to central server continuously, that would mean each one will need uninterrupted internet connectivity. It will end up in consuming huge network bandwidth. Also, sending data over the internet would also involve latency, which at least in certain cases may not be acceptable. All these things are expensive from a business perspective and here Edge Computing comes into the picture.
In this architecture, the collected data is processed near the edge by deploying some compute power – which could be low cost – near to the devices. This is referred as Device Edge. On these local machines, the data received could be received through local networks, not necessarily needing internet. Collected data could be processed near real-time and only actionable data is sent back to the central server immediately. Rest of the data could be archived as per the need on a periodic basis. As you can see, by deploying compute power near the devices, we have addressed all the three issues mentioned above.
There is another variant of Edge Computing. In above example, “Edge” is treated as an edge of the network where devices are located. Whereas in this other variant, “Edge” is treated as an edge of the cloud infrastructure. A close example of this is CDN – the static contents are cached on various edges across the globe and served based on geolocation of the request. However, CDN doesn’t involve any computing power.
There are some concerns about the security of the data at the edge locations, however, with careful planning, those could be handled satisfactorily.