Just as we all were catching up on Web2.0, Web3 has started making rounds. One keeps wondering what this is all about and hence it makes sense go through the history of web to some extent. This article will list lot of new terms and phrases, which I intend to cover in coming days in detail, but for now let’s focus on Web3.
In a nutshell, Web3 is all about decentralization – of ownership, of permissions and of trust. It also brings in some added benefits which we’d see later in the post. However, to understand why decentralization has been the key for Web3, one needs to understand what was original web and Web2.0
The origin
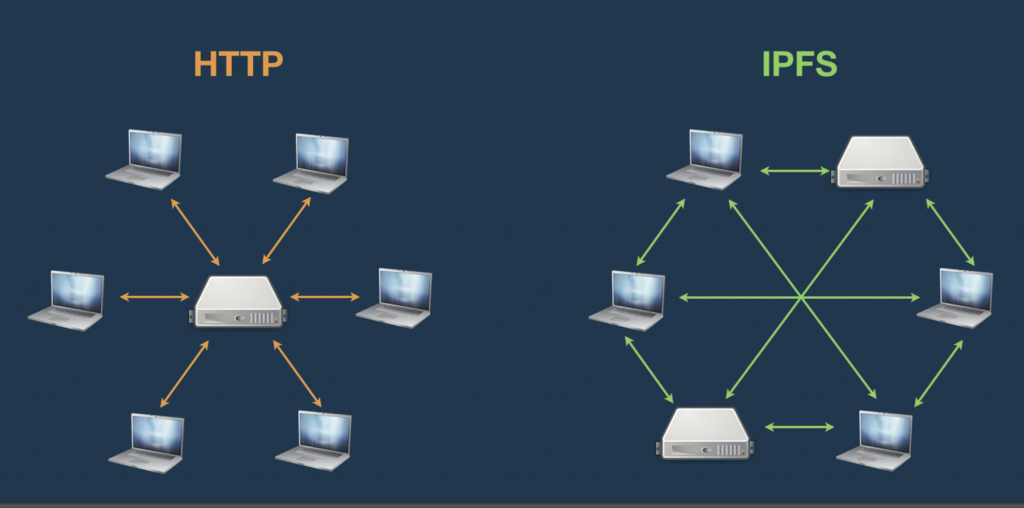
World-wide-web, as it was envisaged was and is a network of connected computers. the early days were primarily “Read-only” as creators used to create content and host that content on their website. The internet consumers use to read the content and were happy with this new information base. There was very little they could do at that point in time.
Evolution
As the user base grew, they wanted to do more with the internet and that gave rise to interactivity on the internet. The “Read-only” web turned into a “Read-Write” web. Social networks gave opportunity to the users to connect with each other and do a lot more than just reading.
However, the idea of “connected” world also gave rise to concentrating power with handful of entities, which could snap the control out of user’s hand in a jiffy. e.g. Trump was banned from Twitter or governments asking social networks to take down specified pages or handles. To some, this was a disturbing development. And this gave rise to next stages in the evolution – decentralization
Current stage – Web3
Web3 represents decentralized internet. You own a piece of the internet and not just consume and produce. In this stage, Blockchain paved the way. Concept of blockchain led to invention of cryptocurrency (Bitcoin to be specific) and the inventors rejoiced with the idea of parallel currency. It also taught the users that the currency or for that matter the data on the internet can be controlled by the public via consensus rather than single or handful of entities. Launch of Ethereum took this concept even further. Even the trust could be decentralized and various folks (or nodes) can reach a consensus about trusting something or not instead of a central authority. This is where the current stage got marked as Web3.

Some distinct advantages of Web3:
- Decentralization
- Permissionless
- Trustless
- Support for native payments
In Web3, typically, your data lives in some or the other blockchain. With Oracles or some similar mechanisms, a blockchain can interact with external world or other blockchain, thereby improving the core concept of decentralization. One can carry their own data from one blockchain to another without needing anyone’s permission.
Limitations and Problems
Although, decentralization is the core idea, the infrastructure where all the data resides, will most likely still be owned by handful of companies (cloud providers OR the service providers where the code base/authentication systems reside). The concepts of Web3 are still complex for majority of the users and kind of act as a deterrent. With current level of technology, the accessibility is still a challenge from cost perspective.
As we have seen the evolution, it is only prudent to believe that all these limitations and problems will be solved in near future to increase the web3 adoption.
Some other important concepts:
- NFT – Non-fungible tokens
- Cryptocurrency
- CryptoExchanges
- Smart Contracts
- Proof of work
- Proof of stake
- DAOs (Decentralized Autonomous Organizations)
Reference Links: